Sending email safely and securely from Office 365 often feels akin to navigating an obstacle course blindfolded. Between spoofed messages, spam filters, and deliverability woes, it’s tough to ensure your important emails reliably reach the intended inbox.
But what if I told you a simple DNS tweak could significantly improve your Office 365 email security and trustworthiness? Enter SPF—the Spoof Police of email authentication.
Once configured properly, SPF becomes your domain’s steadfast guardian, swatting down fraudulent spoofing attempts and clearing the path for your legitimate emails to land securely in recipients’ inboxes.
Intrigued and want to further empower your Office 365 email? Read on as we break down everything you need to know about crafting impenetrable SPF records. We’ll explore how to create, configure, and troubleshoot SPF records for Office 365 like a pro.
Let’s sharpen those DNS skills and get your email authenticated!
What are SPF Records and Why are They Important?
SPF records play a crucial role in email deliverability and security for Office 365 users. But what exactly are they and why should you care about configuring them properly? This section will explain what SPF records are, how they prevent spoofing, and why validating your Office 365 email with SPF is so important.
Definition of SPF Records
SPF stands for Sender Policy Framework. An SPF record is a specific type of DNS TXT record that identifies authorized mail servers for a domain.
In simple terms, an SPF record specifies which servers or IP addresses are allowed to send email on behalf of your domain. Any reputable email coming from your domain should originate from one of the authorized servers listed in the SPF record.
If an email claiming to be from your domain comes from an unauthorized server not specified in the SPF record, the receiving email server will know the email is spoofed or forged.
The SPF record gives instructions for what to do with unauthorized email – commonly to reject or quarantine the message.
How SPF Records Prevent Email Spoofing
Email spoofing, also known as email forgery, is when an email is made to look like it came from someone or somewhere other than the real source. Spoofing tricks recipients into believing a fraudulent email is legitimate.
Spoofing is a common tactic used in phishing campaigns and scams. For example, a spoofed email might appear to come from your bank, even though it actually originated elsewhere.
SPF records combat spoofing by making it harder for scammers to falsify the origin of an email. SPF works together with other email authentication protocols like DKIM and DMARC to validate legitimate emails from your domain.
When your domain has a properly configured SPF record, receiving mail servers can cross-check that incoming mail actually came from one of your authorized servers.
If the source doesn’t match, the email server knows the message has been spoofed and can reject or quarantine it. This prevents fake emails from landing in recipients’ inboxes.
Why Validate Email with SPF for Office 365?
There are a few key reasons why implementing SPF records is recommended for Office 365 users:
- Improve deliverability: Emails failing SPF checks are more likely to be treated as spam. Validating your authorized servers improves inbox placement.
- Combat phishing: Spoofed emails can bypass spam filters. SPF records provide an added layer of protection against phishing scams.
- Protect sender reputation: If others spoof your domain, your reputation suffers when recipients report fake emails. SPF records mitigate this.
- Increase security: SPF works hand-in-hand with DKIM and DMARC to lock down your email authentication and prevent spoofing.
- Reduce administrator workload: Spoofed emails often lead to complaints and tickets for administrators to resolve. SPF records minimize this extra work.
In short, SPF records are a simple way to protect your domain’s sending reputation, enhance email security, and assure recipients your messages come from you. For Office 365 users, having an accurate SPF record configured is essential.
SPF Record Example
To better understand the structure of an SPF record, let’s look at some examples:
SPF Record with Single Authorized Server
v=spf1 ip4:192.168.1.10 ~allBreaking this down:
v=spf1indicates this is an SPF recordip4:192.168.1.10authorizes the mail server with IP address 192.168.1.10 to send mail for this domain~allis a “soft fail” modifier that instructs receivers to allow but flag emails from unauthorized servers
This simple SPF record specifies that the server at 192.168.1.10 is authorized to send email for this domain.
SPF Record with Multiple Authorized Servers
v=spf1 ip4:192.168.1.10 ip4:10.20.30.40 include:servers.example.com -allHere we have:
- Two directly authorized IP addresses
include:servers.example.comto authorize additional servers under that domain-allfor a “hard fail” to reject unauthorized emails
This shows how you can allow multiple authorized mail servers in your SPF record.
The examples demonstrate how SPF records provide instructions to receiving servers for handling emails from your domain. Configuring SPF creates a whitelist of your legitimate mailing servers.

Default Office 365 SPF Record Syntax
When you configure Office 365 for email, a default SPF TXT record is automatically created for your domain. What exactly does this default SPF record contain though and what syntax rules does it follow? This section will break down the components of Office 365’s default SPF record to help you understand how it validates your domain.
Breakdown of Office 365 SPF Record Components
The default Office 365 SPF record generally follows this syntax format:
v=spf1 include:spf.protection.outlook.com -allLet’s walk through what each part means:
v=spf1– Denotes this is a Sender Policy Framework record version 1.include:spf.protection.outlook.com– Authorizes Microsoft’s Office 365 servers to send email by referencing the protection.outlook.com SPF record.-all– The enforcement rule to fail emails from unauthorized servers not matching the SPF record.
This simple default SPF record authorizes Office 365 to send email on behalf of your domain to recipients worldwide.
For Office 365 operated out of Europe or Germany regions, the include mechanism would be include:spf.protection.outlook.de instead.
The -all enforcement rule means emails failing the SPF check will be rejected or marked as spam, providing a “hard fail”. A “soft fail” like ~all can optionally be used.
That covers the basic components of default SPF syntax created for Office 365 domains. But what if you have additional on-premises mail servers to authorize?
Modifying for On-Premises Exchange Servers
If you have a hybrid environment with on-premises Exchange servers alongside Office 365, some modifications are needed.
You’ll need to add the external IP addresses of your on-premises servers to the SPF record.
For example, adding a single on-premises server at IP 1.2.3.4 would look like:
v=spf1 ip4:1.2.3.4 include:spf.protection.outlook.com -all To authorize additional servers, you can include multiple IP4 or IP6 mechanisms:
v=spf1 ip4:1.2.3.4 ip4:5.6.7.8 include:spf.protection.outlook.com -allOr reference entire IP ranges:
v=spf1 ip4:1.2.0.0/16 ip4:5.6.0.0/16 include:spf.protection.outlook.com -allJust be aware SPF records are limited to a maximum of 10 DNS lookups. So use IP ranges where possible when adding on-premises systems.
With this understanding of the default Office 365 SPF record syntax and how to modify it as needed, you can properly configure SPF for your own domain.

Creating or Updating SPF Records in DNS
You understand what SPF records do and the basic Office 365 syntax. But how do you actually go about creating or updating the SPF record in DNS for your custom domain? This process involves gathering key information, carefully forming the full SPF record value, and adding or modifying the TXT record in your DNS management console.
Gather Information Needed for Office 365 SPF
Before creating your SPF record, you need to gather some key information:
The default SPF record value provided by Office 365. This gives you the base to work from.
Any additional mail servers or services sending on your behalf. For hybrid or complex environments, you may need to authorize additional servers beyond Office 365.
Your DNS hosting provider and credentials. This is where you will login to add/edit the SPF record.
Let’s walk through where to find each piece:
Open the Microsoft 365 Admin Center
- Login at admin.microsoft.com with your Office 365 admin credentials.
- Navigate to Setup > Domains in the left sidebar.
- Select your custom domain (not the initial .onmicrosoft.com domain).
Navigate to your domain
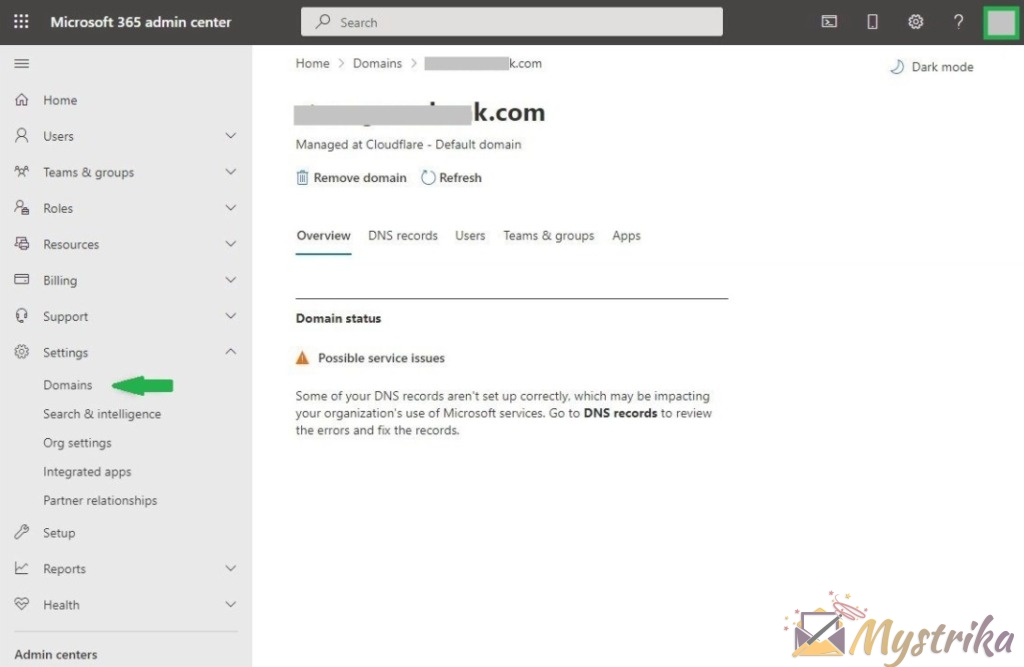
Domain overview in Office 365
This overview will be a good reference later for things like your MX and DKIM records when setting those up.
Lookup the SPF Record
- Click on the DNS Records tab.
- Scroll down to the TXT (SPF) section.
- If a record already exists, click on it to open the details.
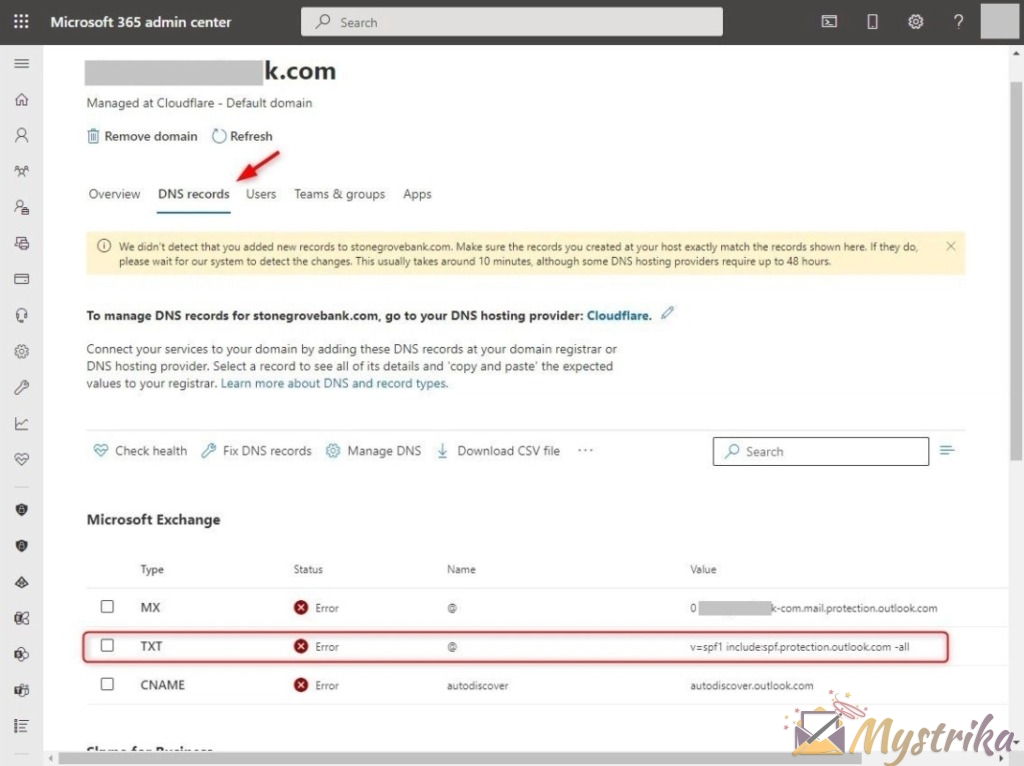
View Office 365 SPF Record
If you see “Invalid Record” in red text, an SPF record exists but needs to be updated with the Office 365 value.
Copy the SPF value
- Copy just the
include:spf.protection.outlook.comportion of the SPF record. - This will be added to any existing SPF record for your domain.
Now you have the default Office 365 SPF record value. Time to determine any other servers that need authorizing.
Form the Full SPF TXT Record
Start by copying your existing SPF record value from your DNS provider’s console into a text file.
If no SPF record exists yet, just put v=spf1 to start a new one.
Now add the required Office 365 include value you copied earlier:
v=spf1 include:spf.protection.outlook.comThen append any additional IP addresses or include mechanisms for on-premises or third-party systems that send mail for you:
v=spf1 include:spf.protection.outlook.com ip4:192.168.1.5 include:mailservice.comFinally, add the enforcement rule on the end (usually -all):
v=spf1 include:spf.protection.outlook.com ip4:192.168.1.5 include:mailservice.com -allDouble-check your assembled SPF record matches legitimate mail servers for your domain. Also ensure you stay under the 10 DNS lookup limit if adding multiple systems.
Add or Update the SPF Record in DNS
Now that the full SPF record value is formed, you need to add or update it in your DNS provider’s management console.
If no SPF record exists yet, follow their instructions to add a new TXT record:
- Type: TXT
- Name/Host: @
- Value: (your full SPF record value)
If an SPF record already exists, edit the existing record to replace the value with your new full one.
Once saved, give it some time to propagate across DNS servers before verifying. SPF records are often updated quickly within minutes, but can take up to 48 hours maximum.
SPF Record Creation for Popular DNS Providers
For convenience, here are quick steps for some popular DNS hosts:
GoDaddy
- Login and go to DNS > Manage Zones
- Select your domain > Records tab
- Scroll down to Text (SPF)
- Click Edit and enter your full SPF value
- Click Save
Namecheap
- Login and go to Domains List > Manage
- Choose your domain > Advanced DNS
- In TXT Records, click Add New Record
- Enter full SPF value and click Save Changes
Cloudflare
- Go to your domain and select DNS
- Click Add record > Text
- Enter @ for the Name and your full SPF value
- Change type to TXT and click Save
Bluehost
- Go to Domains > Manage Domains
- Select your domain > DNS Zone Editor
- Add a new record with type TXT
- Enter @ for host and your full SPF value
- Click Save Changes
And that covers the end-to-end process of gathering information, forming the SPF record, and adding it in DNS for Office 365. Be sure to verify the new record once DNS propagation completes.

Verifying Your Office 365 SPF Record
Once you’ve added or updated the SPF record in DNS, verification is an important next step. You need to confirm the SPF record is syntactically correct, Office 365 is authorized properly, and no common errors exist. Here are some tips for verifying your Office 365 SPF record.
Use Office 365 Admin Center to Check SPF
The Office 365 Admin Center provides an initial status check of your SPF record.
- After DNS propagation, login to admin.microsoft.com and go to Setup > Domains.
- Select your custom domain and click on the DNS Records tab.
- Scroll down and click on the TXT (SPF) record.
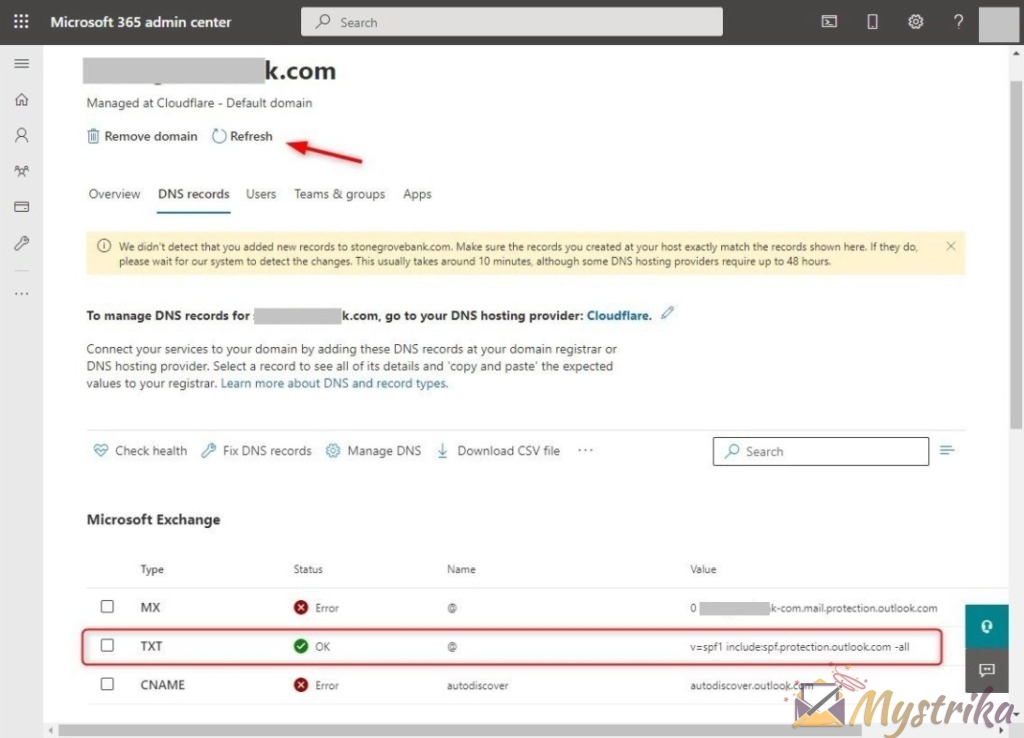
SPF status in Office 365
If the SPF record shows status “Valid” and “Correct” in green text, then Office 365 is authorized properly.
If you see “Invalid Record” in red text, then a syntax error likely exists in your SPF record value. Double check the value you entered in your DNS provider matches the full record assembled earlier.
While useful, the Office 365 checker only validates Office 365 itself is authorized in the record. More extensive validation is recommended…
Validate SPF Record with Online Tools
To perform deeper verification of your SPF record, several free online tools are available:
These tools parse your complete SPF record and highlight any syntax errors or formatting problems. They also check things like:
- Presence of only 1 SPF record for your domain
- Valid IP addresses and domain syntax
- Enforcement rule on the end
- Total DNS lookups under the limit
Simply enter your domain and the tool will lookup and analyze the SPF record automatically, providing detailed results on its correctness.
Fix any errors found before continuing.
Check for and Fix Common SPF Record Errors
Some other common SPF record issues to check include:
No SPF Record Present
If no SPF record is configured yet, sending mail will either fail or be marked as spam by recipients. Follow the steps earlier to add the Office 365 SPF record to DNS.
Multiple SPF Records
There can only be one valid SPF record for a domain. Multiple SPF records will fail checks. Ensure any old SPF records are removed from DNS.
Incorrect Syntax
Typos in the SPF record format will cause validation failures. Double check the syntax matches RFC 7208.
Exceeding 10 DNS Lookups
Too many DNS lookups creates performance issues. Use IP ranges to consolidate entries under the 10 lookup limit.
Omitting Enforcement Rule
Missing the -all or ~all enforcement rule at the end may cause the SPF record to be disregarded.
Invalid IP Addresses
Any typos in authorized IP addresses will result in validation failures. Verify all IPs specified are correct.
Properly verifying your SPF record is vital for ensuring Office 365 mail passes authentication checks and ends up in inboxes where it belongs. Take advantage of the available tools to confirm everything is working as expected.

Combining SPF with DKIM and DMARC for Added Security
While SPF records provide a solid foundation for email authentication, pairing SPF with DKIM and DMARC takes your Office 365 security to the next level. This section provides an overview of DKIM and DMARC, how to configure them alongside SPF, and the combined protection they offer.
Overview of DKIM and DMARC
DKIM and DMARC work hand-in-hand with SPF to validate your emails:
DKIM (DomainKeys Identified Mail) – Cryptographically signs emails to prove they have not been tampered with. The signature validates the message content originated from your authorized servers.
DMARC (Domain-based Message Authentication, Reporting, and Conformance) – Aligns the “From” email domain with the SPF/DKIM validated domain. Preventing domain spoofing.
With SPF, DKIM, and DMARC deployed together, essential components of an email’s authenticity are verified:
- SPF – Confirms authorized sending server
- DKIM – Validates unmodified email content
- DMARC – Matches domain in “From” with validated domain
This provides layered protection against spoofing, tampering, and other threats.
Configuring DKIM and DMARC with Office 365
Luckily enabling DKIM and DMARC in Office 365 is straightforward:
DKIM
- In the Office 365 Admin Center, go to Setup > Domains and choose your domain.
- Click Add record under Domain Key Identification (DKIM).
- Leave the default Selector and Token values.
- Click Save and let the TXT record propagate.
That’s it! DKIM is now active for your Office 365 domain.
DMARC
- Go to Setup > Domains and choose your domain.
- Click Add record under Domain-based Message Authentication (DMARC).
- Replace “v=DMARC1” with:
v=DMARC1; p=none; pct=100; ruf=mailto:[email protected]; rua=mailto:[email protected]- Click Save and let the TXT record propagate.
This enables DMARC in monitor-only mode initially. Once you verify SPF and DKIM are working, come back and set p=reject or p=quarantine to enforce DMARC protections.
And with those simple steps, you’ve implemented the email authentication trifecta!
How SPF, DKIM and DMARC Work Together
Let’s walk through how the technologies authenticate an inbound email to your Office 365 mailbox:
- Email is received from an external sender to your custom domain.
- SPF check – Receiving server validates the sending server IP is authorized in your SPF record.
- DKIM check – DKIM signature is decrypted to verify email content is unmodified.
- DMARC check – SPF and DKIM results are combined to confirm “From” domain matches your real domain.
- Email passes checks and is delivered to your inbox!
If any part of this chain fails, the email is rejected or quarantined accordingly.
For example, an attacker spoofing your domain would fail SPF since their unauthorized server IP doesn’t match.
Or a phishing email sent from a compromised account would fail DKIM since the content was maliciously modified.
Enabling this layered email authentication approach provides strong protection against threats. SPF records lay the foundation, enhanced by DKIM and DMARC.
Some key benefits of combining the technologies include:
- Minimized spoofing and phishing attacks
- Reduced impact of compromised email accounts
- Improved inbox placement and deliverability
- Less unwanted messages reaching recipients
- Better visibility into authentication failures
If you haven’t set up DKIM and DMARC yet, do so in conjunction with SPF for robust email security. And remember to monitor DMARC reports to ensure everything is working smoothly.
With SPF, DKIM, and DMARC properly configured, you can rest assured your Office 365 email is protected.

Maintaining Your SPF Record Over Time
Setting up your Office 365 SPF record is an important first step. But maintenance is also crucial to keep your SPF record accurate and effective as changes occur. This section covers best practices for auditing, updating, and staying current with your SPF record.
Regularly Audit SPF Record Accuracy
It’s good practice to periodically audit your SPF record to ensure nothing has gone stale. Perform these review checks at least annually:
- Reconfirm all authorized servers are still active and should remain in the SPF record. Remove any decommissioned or expired systems.
- Verify domain names of third-party systems are still correct and valid. Update any that changed.
- Check if your account was migrated to new Office 365 infrastructure. If so, update the include domain.
- Revalidate the overall syntax for any mistakes that crept in.
- Test the SPF record with online tools to check for issues.
- Review DMARC reports for any failures caused by SPF not aligning.
Regular audits give you visibility into lingering SPF problems before they impact email delivery.
Update for Changes Impacting Email Delivery
Be alert for events that should trigger an SPF record update:
- New mail servers or services come online that need authorizing in SPF.
- On-premises mail servers get reassigned to new IP addresses.
- Email sending domains/subdomains get added or reconfigured.
- Office 365 tenants are consolidated or migrated between geographic regions.
- Third-party email services associated with the domain are changed.
Carefully evaluate how major infrastructure or provider changes impact SPF. Modify your SPF record value as needed to keep it accurate.
Think holistically about your overall email ecosystem, not just Office 365 in isolation.
Keep Current on Best Practices for Office 365 SPF
SPF record best practices evolve over time. To stay up to date:
- Review Microsoft’s latest guidance in the Office 365 documentation.
- Monitor blogs/forums focused on Office 365 email and security.
- Use RFC 7208 as the SPF syntax reference standard.
- Only make incremental changes when troubleshooting delivery issues or optimizing performance.
- If switching DNS providers, transfer SPF and other records carefully.
- Keep your SPF record value under 255 characters.
- Stay under the 10 DNS lookup limit when adding multiple mechanisms.
Applying new recommendations or learnings from the community will keep your SPF record aligned with current best practices. Avoid major overhauls unless necessary.
Maintaining your Office 365 SPF record requires occasional audits and updates. But doing so ensures your email authentication remains effective over time.
Key Takeaway
Properly configuring SPF records is vital for securing Office 365 email and improving deliverability. The key steps covered in this guide include:
- Understanding how SPF prevents email spoofing by whitelisting authorized mail servers
- Adding the required Office 365 include mechanism to your SPF record
- Incorporating any on-premises or third-party servers also sending mail
- Creating or updating the TXT record in your DNS management console
- Validating your SPF record using online tools to confirm accuracy
- Pairing SPF with DKIM and DMARC for layered email authentication
- Performing periodic audits to keep your SPF record current over time
Following this comprehensive SPF setup process will authenticate your custom domain, stop spoofers, and ensure your important Office 365 emails reliably reach the inbox. Configuring SPF records is a straightforward way to boost email security.
Frequently Asked Questions about Office 365 SPF
SPF records are a key part of securing your Office 365 email. But lots of common questions arise on properly configuring and troubleshooting them.
This extensive FAQ covers many of the frequent SPF issues Office 365 administrators may encounter:
Q: Why do I need an SPF record for Office 365?
A: SPF records help validate your outgoing Office 365 emails by identifying authorized sending servers. This prevents spoofing and improves deliverability. Microsoft requires SPF records when using custom domains in Office 365 for this reason.
Q: Is the Office 365 SPF record created automatically?
A: Yes, Office 365 automatically creates a minimal SPF record including their servers when you configure your custom domain. But you still need to verify and possibly modify it.
Q: What is the default Office 365 SPF record syntax?
A: The basic default syntax is v=spf1 include:spf.protection.outlook.com -all to authorize Office 365 servers. For Office 365 Germany, the syntax is v=spf1 include:spf.protection.outlook.de -all.
Q: What if I use third-party email services too?
A: You’ll need to add additional include or ip4 mechanisms to authorize any third-party mail services also sending on your domain’s behalf.
Q: Can I validate both Office 365 and G Suite?
A: Yes, combine both companies’ include statements, for example: v=spf1 include:spf.protection.outlook.com include:_spf.google.com -all
Q: How do I add my on-premises servers?
A: List your on-premises server IP addresses with ip4 tags, like: ip4:192.168.1.55 ip4:192.168.1.77.
Q: Where do I actually create the SPF record?
A: SPF records are created in your external DNS zones, using your domain registrar or DNS host’s management console.
Q: What type of record is an SPF record?
A: SPF records are a type of DNS TXT record. When adding a new SPF record, you’ll create a TXT record with your assembled SPF value.
Q: How long does an SPF record update take to update?
A: DNS propagation usually completes within minutes, but can take up to 48 hours. Check multiple times before troubleshooting.
Q: Can I have more than one SPF record?
A: No, only one SPF record is allowed per domain. Multiple SPF records will fail causing authentication issues.
Q: What is the lookup limit for SPF records?
A: SPF records are limited to a maximum of 10 DNS lookups. Exceeding this limit will cause failures.
Q: Why does my SPF record show invalid syntax?
A: Syntax errors like incorrect formatting will cause SPF validation failures. Double check your record matches proper SPF syntax per RFC 7208.
Q: How do I troubleshoot SPF related email delays?
A: Tools like digwebinterface can help diagnose SPF issues. Check that only one SPF record exists and receiving servers are respecting it.
Q: What does an SPF “temperror” mean?
A: A temperror indicates the receiving server had a temporary DNS failure while validating SPF. The email may still be delivered.
Q: Why are SPF “softfail” results not spam?
A: A softfail only flags the email, but does not reject it. So messages may still be delivered unless your spam filter is configured aggressively.
Q: How does SPF deal with forwarded email?
A: When an email is forwarded outside of Office 365, the SPF check evaluates the final sending server rather than the original one.
Q: Is SPF evaluation case-sensitive?
A: No, SPF record formatting is not case-sensitive. v=spf1 is treated the same as V=SPF1.
Q: Can I test SPF without impacting users?
A: Yes, use ?all instead of -all or ~all while testing to avoid spam foldering messages that fail.
Q: Will SPF alone stop 100% of email spoofing?
A: No, SPF is not bulletproof by itself. Use it alongside DKIM and DMARC for layered email authentication and maximum protection.
Hopefully these common SPF questions and answers will provide you with a better understanding of how to properly configure and troubleshoot SPF records for Office 365. Reach out for additional help if needed!

